We are glad to announce that today we officially started supporting TLS 1.3 and 0-RTT implementation for it.
Our clients are going to enjoy the great speed and security improvements coming from the upgrade.
For those of you, that are not-so-familiar with the technological slang, here is a reminder, what are those, and why are they so important:
TLS (Transport Layer Security) 1.3 is the latest step in the evolution of internet data transfer securitization protocols. Basically, the main advantage compared to the older – 1.2 version of the protocol is that much of the old features used in desperate attempts to support older browsers are simply removed. And yes – it is OK. Even if anyone still uses them, very soon nobody will!
Why were those removed, you’ll ask? Well, simply put – those features were the main reasons for some of the biggest security failures of our time. Here’s some of them:
- RSA key transport
- CBC mode ciphers
- RC4 stream cipher
- SHA-1 hash function
- Arbitrary Diffie-Hellman groups
- Export ciphers
The hidden bonus of implementing the TLS 1.3 is the speed!
Nowadays with 2 out of 3 web-searches made from a mobile device, fast browsing is the next big thing. People are just not willing to wait anymore.
From the other hand, every secured connection between the browser and a website consists of multiple “messages” or “round-trips” ( to accomplish cryptographic handshake). With the older TLS 1.2, the number of round-trips needed to complete the handshake was 2. With the newer version 1.3, the number is half that – one! Which in terms of time – yes you guessed right – is twice as fast!
Now add to that the fact that for a browser to download a web page over HTTPS, there are 4 things that need to happen the first time your browser tries to access a site:
- DNS Lookup
- TCP Handshake
- TLS Handshake
- HTTP Request and responce
…and those 4 things “cost” you 4 round-trips!
The good news is that with the TLS 1.3 you save one Round-trip and the final score is 3!
Ok but How?
Remember those removed useless features from earlier? With them gone, there’s simply no need for the second round-trip during the TLS handshake.
OK, but we want more…
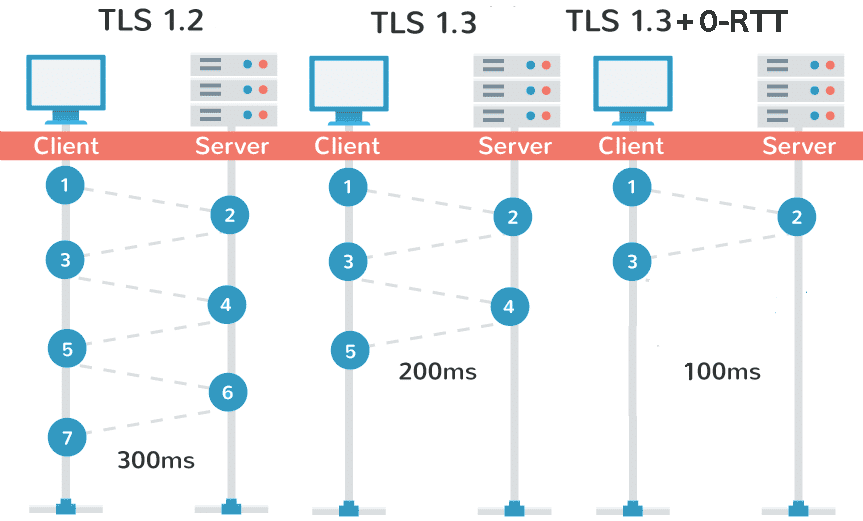
0-RTT or “Zero Round Trip Time resumption” – stands for all those connections to a site, that are happening for the second time after a short period of time, which basically means they simply are resuming a previous connection.
Nowadays around 40% of all connections fall into this category.
Now imagine if you could have a tool to optimize 40% of all the connections on the internet!
That’s right – 0-RTT does exactly that! With it, you can send the first request to the server before the TLS connection is fully established which results in even faster load times, speeding up resumed connections, leading to a faster and smoother web experience for websites that people visit regularly. (This is even more important for the mobile networks.)
If we get back to our mathematics from earlier – now the numbers look differently – for all those resumed connections (that use the TLS 1.3 + 0-RTT) the number of round-trips is now 2
Having that in mind, this unique combination truly is a big step for humanity and it’s ability to connect fast!
How to enable TLS 1.3 and 0-RTT in your browser:
TLS 1.3 is currently supported in both Chrome (starting with release 66) and Firefox (starting with release 60), and in development for Safari and Edge browsers.
For Chrome:
- In the address bar, enter chrome://flags and press Enter.
- Scroll to locate the TLS 1.3 entry, and set it to Enabled. You will say a message saying that the change will take effect the next time you relaunch Chrome.
- Click RELAUNCH NOW to re-start Chrome.
After enabling TLS 1.3, visit a site with TLS 1.3 enabled over HTTPS. Then:
- Open Chrome Developer Tools.
- Click the Security tab.
- Reload the page (Command-R in Mac OS, Ctrl-R in Windows).
- Click on the site under Main origin.
- Look on the right-hand tab under Connection to confirm that TLS 1.3 is listed as the protocol.
For Firefox:
- In the address bar, enter about:config and click to accept the warranty warning.
- Search for security.tls.version.max and set it from the default value of 3 to 4.
After enabling TLS 1.3, visit a site with TLS 1.3 enabled over HTTPS. Then:
- Click the green lock icon in the address bar, then >.
- Click More Information.
- Under Technical Details, verify that the TLS version is TLS 1.3.
If you have any questions or need further clarification about our services and how you could get most out of the new technology, please, do not hesitate to contact us via our website – https://ucdn.com
Get a FREE Welcome Bonus to test our services.
Sign Up for a FREE CDN START